Subscription-Based Managed Cloud Service
Delivered as a cloud service, USM Anywhere deploys rapidly and enable you to start detecting threats within minutes.
USM Anywhere’s subscription-based pricing making it affordable for even small IT security teams to get started with a with a low-risk, minimal investment.
With no hardware appliance to install or maintain in your data center, you save significant time, resources, and money for an overall low total cost of ownership.
incorporating multiple essential security capabilities in one unified platform, USM Anywhere simplifies and accelerates threat detection, incident response, and compliance management for today’s resource-constrained IT security teams.
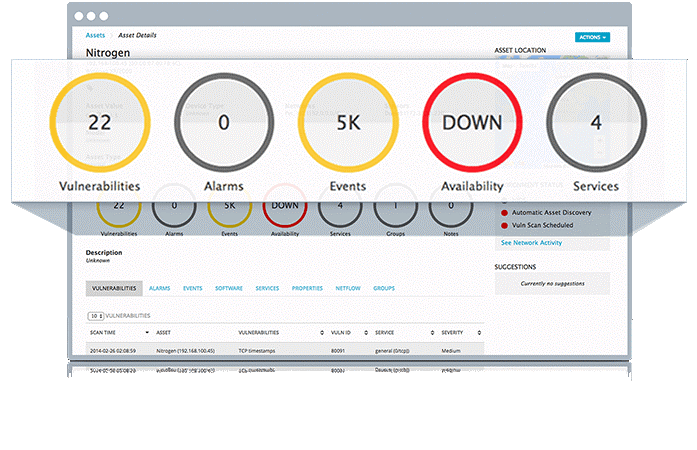
USM Anywhere Sensors & AlienVault Agents
USM Anywhere uses virtual sensors that run on VMware and Microsoft Hyper-V to monitor on-premises physical and virtual IT infrastructure. In the cloud, lightweight cloud sensors natively monitor Amazon Web Services and Microsoft Azure Cloud.
In addition, AlienVault Agents can be deployed on Windows and Linux endpoints. Security analysis and log storage are centralized in the AlienVault Secure Cloud and Atlantic provides you with centralized security visibility of your critical infrastructure.