Cybersecurity is a constant contest between attackers and defenders. One side searches for gaps. The other works to close them. This cycle has been repeating for decades, but the pace is accelerating.
The attacks that once seemed rare are now a daily occurrence. The tools that once protected businesses are no longer enough on their own. By 2026, threats will be sharper, defenses will be more complex, and the consequences of falling behind will be far greater.
The best way to prepare is not to guess, but to pay attention to the patterns that are already emerging. The future of cybersecurity is not written in stone, but the trends are clear. Here is what the next chapter is likely to bring.
Smarter Cyber Threats Are Coming
Every year, this prediction makes the list: the coming year promises an increase in more sophisticated attacks. Criminals are developing tools that can adapt, disguise themselves, and slip past traditional defenses. Phishing messages now appear genuine, and fake audio or video can easily mimic the voices of trusted individuals.
By 2026, these threats will evolve more rapidly and with greater precision. They will adjust in real time, making older security approaches far less reliable. Organizations will need to invest in constant monitoring, quicker detection methods, and response strategies that can contain an attack before it spreads.
Zero Trust Becomes the Standard
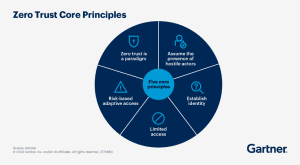
Zero Trust has been a security concept for years, but in practice, many organizations have only partially adopted it. The idea is straightforward: no user or device should be trusted automatically, even if it is inside the network. You must verify each request before granting access.
By 2026, Zero Trust will shift from being a best practice to being the expectation. Regulations will compel industries that handle sensitive data to implement it, and insurers and clients will begin to require it. The model itself will also grow more advanced, relying on continuous checks of identity and behavior rather than one-time logins. For businesses, adopting Zero Trust will become less about getting ahead and more about keeping up.
Quantum Computing Threatens Encryption
Quantum computing has often been discussed as a distant possibility, but its impact on cybersecurity is severe enough that organizations are already preparing for it. The encryption methods that protect online banking, government systems, and private communications could one day be broken by powerful quantum machines.
By 2026, we are unlikely to see quantum computers cracking into networks on a large scale. What we will see is the steady rollout of post-quantum cryptography. Governments, banks, and healthcare providers are beginning to test algorithms designed to withstand quantum threats, and vendors will be expected to follow. Businesses that ignore this shift risk falling behind the curve when quantum security becomes the new standard.
The Cloud Will Define Cybersecurity
Most organizations already use the cloud in some form, whether for email, file storage, or business applications, and by 2026, that reliance will be nearly universal. This shift changes how we must manage security. Protecting a single office network is no longer enough when you have applications, data, and users across multiple cloud platforms.
The focus will shift toward cloud-native security tools that can protect workloads regardless of their hosting location. Solutions like Secure Access Service Edge (SASE) and cloud-based firewalls will become the standard, enabling businesses to manage identity, access, and data protection in a single location. Companies that continue to rely solely on perimeter defenses will be more vulnerable, as the traditional concept of a network boundary continues to evolve.
Ransomware Evolves Into Multi-Layered Extortion
Ransomware has moved far beyond simply locking files and demanding payment. Today, many attackers also steal data, threaten to release it publicly, or directly pressure customers and partners. This layered approach has made ransomware one of the most damaging and costly threats facing businesses.
By 2026, we anticipate that ransomware will continue to evolve into even more sophisticated forms. Attackers will target supply chains, cloud platforms, and even proprietary models or software that companies depend on. Organized groups will continue to sell ransomware kits as a service, making it easier for less-skilled criminals to launch large-scale attacks. To prepare, businesses will need strategies that include strong backups, rapid detection, and response plans that limit the spread before the damage is done.
Regulations and Cyber Insurance Shape Security
Governments are becoming more involved in cybersecurity, recognizing that weak defenses in one business can create risks for entire industries. By 2026, regulations will impose stricter requirements on how organizations handle data, particularly in sectors such as healthcare, finance, and energy. Compliance will no longer be optional or limited to large enterprises.
At the same time, cyber insurance is changing the way companies approach security. Insurers are raising their standards, requiring proof of practices such as regular patching, employee training, and the use of frameworks like Zero Trust before offering coverage. Together, regulation and insurance will encourage businesses to strengthen their defenses, not only to avoid penalties but also to remain eligible for protection in the event of an attack.

IoT and Edge Device Security Take Center Stage
The number of connected devices continues to rise in nearly every industry. Hospitals use connected medical sensors, manufacturers rely on innovative equipment, and schools adopt digital tools that run on networks. Each of these devices creates another opening for bad actors.
By 2026, securing these devices will become a top priority. Attacks on critical infrastructure through vulnerable sensors or controllers are no longer hypothetical, and the risks will grow as more devices come online. Businesses will need to manage updates across thousands of endpoints, enforce stronger authentication, and closely monitor device activity. New standards for IoT security are likely to emerge, and organizations that fail to comply may face both regulatory issues and increased exposure.
The Human Factor in Cybersecurity
Even the strongest defense can be undone by a simple mistake. A rushed employee clicking a link, reusing a weak password, or ignoring a security update can create an opening that technology alone cannot close. Cybercriminals are aware of this, which is why social engineering remains one of the most effective methods for gaining access.
By 2026, organizations will place greater emphasis on cultivating a culture of security, rather than relying solely on technical safeguards. Training will move beyond check-the-box exercises and focus on everyday habits, such as verifying unusual requests, questioning unexpected emails, and reporting suspicious activity without fear of retribution or blame. The goal is not just to educate but to make security part of the routine. People will remain a risk, but they can also become one of the strongest lines of defense if equipped with the proper awareness and support.
Fewer Tools, More Integration
Many organizations have collected a wide range of security tools over the years. Each one promises to solve a specific problem, but together they create a patchwork that is hard to manage. With multiple dashboards, alerts, and overlapping features, teams often miss the bigger picture.
By 2026, the focus will shift toward platforms that combine protection in one place. Businesses will seek solutions that integrate monitoring, detection, compliance, and response capabilities, rather than relying on separate products. For small and mid-sized companies, Managed Security providers will become an attractive option, offering professional oversight without the expense of building a large in-house team.
Automation Strengthens Cyber Defenses
The scale and speed of modern threats make it impossible for people to handle every alert on their own. Security teams are turning to automation to help close the gap. Tools that can recognize unusual activity, investigate the cause, and even take immediate action are becoming more common.
By 2026, automation will be woven into the core of cybersecurity operations. Instead of sifting through endless warnings, security teams will rely on systems that highlight genuine threats and respond in seconds. The challenge will be finding the right balance: automation can ease the burden and improve response times, but it cannot replace the judgment and context that human oversight provides.
How Businesses Can Prepare for the Future of Cybersecurity
The future of cybersecurity will not be simple. Smarter threats, emerging technologies, and a growing number of connected systems will shape it. The organizations that adapt early will be the ones best positioned to stay secure.
Steps to consider include:
- Moving toward Zero Trust security
- Reviewing cyber insurance requirements
- Planning for post-quantum cryptography
- Strengthening cloud and IoT protections
- Providing ongoing employee training
- Simplifying security with integrated platforms
The choices businesses make today will determine how well they can withstand the challenges of 2026. Those who prepare now will be ready to respond quickly and protect what matters most when new threats emerge.
About Atlantic, Tomorrow’s Office
Atlantic, Tomorrow’s Office is a leading managed services provider offering managed IT, cybersecurity, office technology, business consulting, and digital transformation solutions. Focusing on helping mid-market businesses optimize their cybersecurity practices, enabling technology and operations, Atlantic delivers end-to-end solutions tailored to the evolving needs of today’s enterprises.
For the latest industry trends and technology insights, visit ATO’s main Blog page.